The impact of a security breach can be extremely detrimental, causing significant business interruption and leading to complex forensic and legal matters. As a result, cyber insurance has emerged as a critical component of any organisation’s risk management strategy. This article will explore the current scenarios surrounding cyber insurance, discuss essential cyber cover must-haves, and discuss key considerations and solutions to ensure comprehensive cyber protection.

The Current Scenario
| The landscape of cyber risks is constantly evolving, necessitating organisations to remain vigilant in assessing their cyber risk exposures and management strategies. It is crucial to understand the latest trends in cyber-attacks and the tactics employed by external threat actors, to ensure effective defense mechanisms. Cyber risks are not limited to external threats but also encompass risks arising from within, such as employee negligence or malicious intent. With the rise of remote workforces, businesses must adapt their strategies to mitigate the increased cyber threat. | The insurance industry is facing a significant impact due to the escalating risk of cyber-attacks. Global projections by Cybersecurity Ventures indicate that cybercrime is set to reach an astounding $10.5 trillion annually by 2025, a substantial surge from $3 trillion in 2015. As a result, cyber insurance premiums are on the rise, and insurers are exercising greater caution in selecting the risks they take on due to capacity. |
Cost of Cybercrime in Australia
| The Australian Cyber Security Centre reported receiving over 76,000 cybercrime reports between July 2021 and June 2022, equating to a cybercrime report every seven minutes.” These numbers highlight the pressing need for robust cyber risk management strategies.
The financial implications of cybercrime are significant. The average cost per cybercrime report has surpassed $39,000 for small businesses, $88,000 for medium-sized businesses, and exceeded $62,000 for large businesses—an alarming 14% increase on average.
“The Australian Cyber Security Centre reported receiving over 76,000 cybercrime reports between July 2021 and June 2022, equating to a cybercrime report every seven minutes.”
| Additionally, cyber-attacks can have far-reaching consequences, damaging a company’s reputation and resulting in legal liabilities. Compliance with data protection regulations, such as the Australian Privacy Act, further underscores the importance of effective cyber risk management.
Even professional organisations with reasonably mature cybersecurity programs are not immune to cyber-attacks. In the past year, highly established organisations including Medibank, Optus, HWL Ebsworth and Woolworths have been caught up in substantial data breaches, and the list continues to grow daily. According to the Office of the Australian Information Commissioner Notifiable Data Breaches Report: July to December 2022, 497 notifications were issued, up 26% compared to the previous period.
It’s interesting to note that the sources of data breaches were predominantly 350 (70%) malicious or criminal attacks, 123 (25%) human errors, and 24 (5%) system faults.
|
Directors’ Duties Apply to Cyber
| In line with the Corporations Act, directors and officers carry a fiduciary responsibility to manage risks, including cyber risks. Failure to do so can result in significant financial losses, reputational damage, and potential legal action. It is incumbent upon directors and officers to ensure the implementation of robust cyber risk management strategies and remediation plans . This responsibility also extends to Supply Chain Management, and all organisations whom interact, store or otherwise manage corporate data. | PwC collaborated alongside the World Economic Forum, The National Association of Corporate Directors, The Internet Security Association, and other partners of the WEF to create a set of six agreed-upon principles. These principles have been crafted to aid corporate boards in overseeing a resilient cybersecurity strategy while simultaneously advancing strategic objectives. |
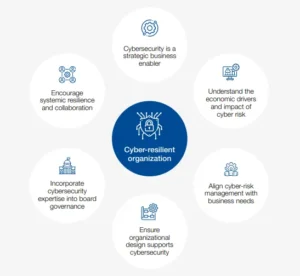
The Value to the Board
| For boards and executive leadership, recognising the value of Cyber Insurance is not merely an exercise in risk management but a strategic imperative. Here’s why:
1. Financial Protection: Cyber Insurance provides a financial safety net in the aftermath of a cyber incident. This ensures that the organisation can continue its operations and recover without facing crippling financial losses.
2. Risk Transfer: Cyber Insurance effectively transfers the financial risk associated with cyber threats to the insurer. This means that in the event of a cyber incident, the burden of financial responsibility is shared with the insurance company, relieving the organisation’s balance sheet. | 3. Compliance and Regulatory Support: In an era of evolving data protection regulations, Cyber Insurance policies often come with built-in compliance support. This can assist organisations in navigating the complex landscape of data privacy regulations and avoiding costly fines.
4. Reputation Management: Beyond financial aspects, Cyber Insurance can contribute to effective reputation management. Boards understand that a tarnished reputation can have lasting repercussions. Having insurance in place to cover public relations and reputation management costs is invaluable.
5. Risk Mitigation: Boards can actively participate in risk mitigation strategies by leveraging Cyber Insurance. Insurers often provide guidance on cybersecurity best practices and risk. |
Tightening Cyber Insurance Market
| Insurers are adopting a more cautious approach, becoming increasingly selective about the risks they underwrite. Organisations lacking adequate cyber risk management strategies may find it challenging to secure comprehensive cyber insurance coverage. Insurers now seek mature and robust cyber risk management strategies capable of mitigating potential losses.
Cyber & Data/Privacy Risk Management has quickly become the most prominent exposures, especially in the financial / AFSL space where data breaches are unfortunately common.
We refer to the case against RI Advice who were found to have breached their license obligations to act efficiently and fairly when it failed to have adequate risk management systems to manage its cybersecurity risks. | Successfully managing cyber risks requires a comprehensive and proactive approach. It involves integrating cybersecurity into the organisational culture and surrounding oneself with knowledgeable professionals who can provide guidance and support.
“ASIC is strongly encouraging all entities to follow the advice of the Australian Cyber Security Centre and adopt an enhanced cybersecurity position to improve cyber resilience in light of the heightened cyber-threat environment.”
To become an attractive risk for insurers, organisations must demonstrate a mature and robust cyber risk management strategy. This includes implementing best practices, compliance frameworks, and ongoing monitoring to stay ahead of emerging threats. Having good governance, a well-defined cyber risk management plan, and adequate cyber insurance coverage are paramount. Organisations should establish policies, define roles and responsibilities, and ensure ongoing compliance with regulations. A comprehensive cyber risk management plan should be developed, regularly reviewed, and updated to adapt to changing threats . It is no longer the purview to say all security is managed by an IT Support Firm. |
Cyber Risk Management Tips
| To effectively address cyber risks, organisations must embrace a minimum level of security, including: |
Multifactor Authentication
| Implementing multifactor authentication (MFA) or two-factor authentication (2FA) adds an extra layer of security, preventing unauthorised access to sensitive information and systems. | It requires users to provide an additional level of authorisation, such as a unique code sent to their mobile device, before accessing a system or application. |
Cyber Security Framework
| Adhering to a comprehensive cybersecurity framework, such as essential 8 principles provides organisations with a systematic approach to managing cybersecurity risks. | These frameworks help identify and prioritise risks, establish policies and procedures, and implement controls to mitigate vulnerabilities. |
Zero Trust Architecture
| Embracing a Zero Trust Architecture is crucial in today’s cyber landscape. This cybersecurity model assumes that all users, devices, and networks are untrusted. | It requires continuous verification of identity, authorisation, and authentication before granting access to any resources, reducing the risk of unauthorised access and lateral movement within the network. |
Vendor Risk Management Programme
| Third-party vendors can introduce potential vulnerabilities, making it essential to have a robust vendor risk management program. This program enables organisations to identify, assess, and manage risks associated with their vendors. | It ensures that vendors comply with cybersecurity requirements and have adequate controls in place to protect sensitive data. |
Effective Incident Response Plan
| Having a well-defined incident response plan is crucial for minimising the impact of a cyber-attack. This plan outlines the steps an organisation should take in the event of a security incident, including detecting, containing, and mitigating the effects of the breach. | An effective incident response plan can help reduce downtime, minimise data loss, and facilitate a quicker recovery. |
Security Awareness Training for Staff
| Employee negligence or malicious intent remains a significant cyber risk. Providing comprehensive security awareness training equips employees with the knowledge and skills to identify and report suspicious activities. | Regular training ensures that employees understand their role in protecting sensitive data and helps create a culture of cybersecurity within the organisation. |
Regular Penetration Testing Schedule
| Penetration testing, also known as ethical hacking, simulates real-world cyber-attacks to identify vulnerabilities and weaknesses in an organisation’s systems. | Regularly conducting penetration tests allows organisations to identify and address potential vulnerabilities before malicious actors exploit them. |
Reliable Data Backup and Process Plan
| Data backups are crucial for recovering from a ransomware attack or other data loss incidents. | Organisations should establish a reliable data backup strategy that includes backup testing, regular backups, risk appraisal and offsite storage to ensure data integrity and facilitate recovery in the event of a cyber incident . |
Take Action Today
| In an increasingly digital landscape, cyber insurance is an essential tool in protecting businesses from the devastating consequences of cyber-attacks.
By embracing cyber cover must-haves and implementing robust cyber risk management strategies, organisations can strengthen their defenses and mitigate potential losses. Working with experts like KBI ensures access to tailored cyber insurance solutions and valuable guidance throughout the process. Don’t leave your business vulnerable to cyber threats—take action today to safeguard your digital future.
At KBI, our expert brokers understand the unique risks businesses face. We provide guidance, assist with the submission process, and offer a clear breakdown of available options when it comes to the insurance market. | In the event of a claim, our experienced team works alongside insurers and incident response teams to ensure a smooth process. The insurers we work with in the cyber market offer 24/7 emergency incident response at no extra cost, helping you mitigate the impact of a cyber event and get back to business.
Contact KBI today to discuss your insurance needs and secure a tailored program that safeguards your organisation. |



